Projects
Light Commands: Laser-Based Audio Injection (2019-Present)
 Voice Assistants such as Alexa, Siri, and Google Assistant have become more popular in recent years, as there is a push to interact with computing systems with natural language. The voice assistants can work on phones and smart speakers to perform various actions with the power of a user’s voice. In combination with other smart home devices, this currently includes: playing music, making purchases from online stores, setting indoor temperatures, opening doors with smart locks, opening garage doors, unlocking car doors, and more. Using modulated laser light as a means for acoustic signal injection into MEMS microphones, we show that the privileges of a user’s voice can be exploited from long distance, presenting a vulnerability inherent to MEMs microphones. By investigating the vulnerability, defenses can be developed to prevent future attacks. See more at lightcommands.com.
Voice Assistants such as Alexa, Siri, and Google Assistant have become more popular in recent years, as there is a push to interact with computing systems with natural language. The voice assistants can work on phones and smart speakers to perform various actions with the power of a user’s voice. In combination with other smart home devices, this currently includes: playing music, making purchases from online stores, setting indoor temperatures, opening doors with smart locks, opening garage doors, unlocking car doors, and more. Using modulated laser light as a means for acoustic signal injection into MEMS microphones, we show that the privileges of a user’s voice can be exploited from long distance, presenting a vulnerability inherent to MEMs microphones. By investigating the vulnerability, defenses can be developed to prevent future attacks. See more at lightcommands.com.
Sensor Security of LiDAR in Autonomous Vehicles (2018-2019)
 LiDAR sensors are used as a foundation of perception in Autonomous Vehicle prototypes. But the data
acquired by LiDAR have been shown to be affected by a variety of physical phenomena. If a malicious
agent can perform these physical attacks, they can potentially cause a collision and threaten the
safety of the passenger. If we can discover what capabilities an attacker may possess with these
attacks, we can develop ways to defend against them.
LiDAR sensors are used as a foundation of perception in Autonomous Vehicle prototypes. But the data
acquired by LiDAR have been shown to be affected by a variety of physical phenomena. If a malicious
agent can perform these physical attacks, they can potentially cause a collision and threaten the
safety of the passenger. If we can discover what capabilities an attacker may possess with these
attacks, we can develop ways to defend against them.
Firmware Obfuscation for Embedded Devices (2018-2019)
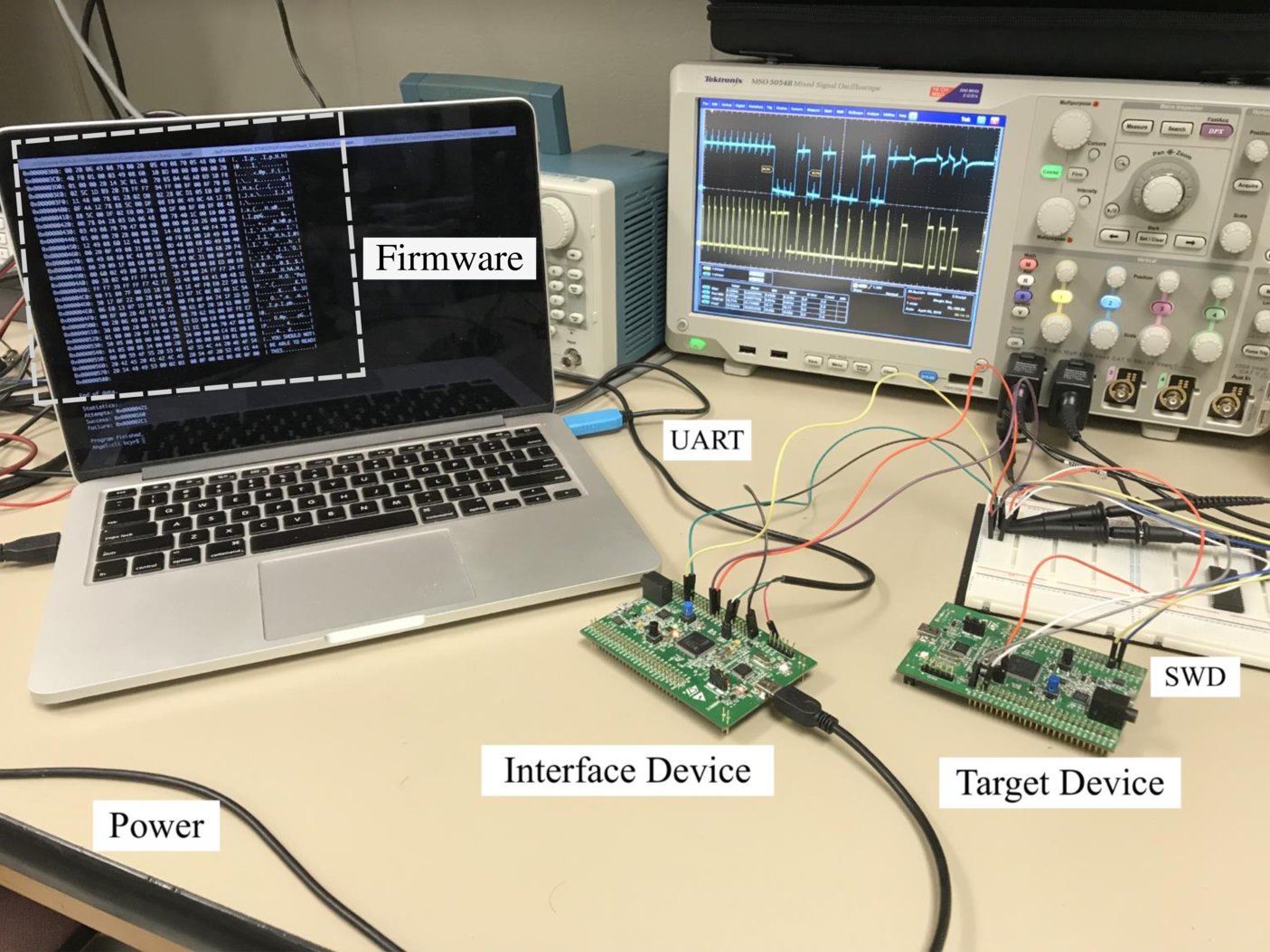 Due to limited resources, embedded devices have limited protection against cloning and firmware
extraction. To help prevent this kind of attack, an obfuscation technique was developed to rearrange
the order of instructions in the firmware. Using a small cache, a real device can reconstruct the
firmware. Without the correct Device ID, it will be difficult for a cloned device to reconstruct
the firmware.
Due to limited resources, embedded devices have limited protection against cloning and firmware
extraction. To help prevent this kind of attack, an obfuscation technique was developed to rearrange
the order of instructions in the firmware. Using a small cache, a real device can reconstruct the
firmware. Without the correct Device ID, it will be difficult for a cloned device to reconstruct
the firmware.
Optimal Sampling for Sensing Systems (2017-2019)
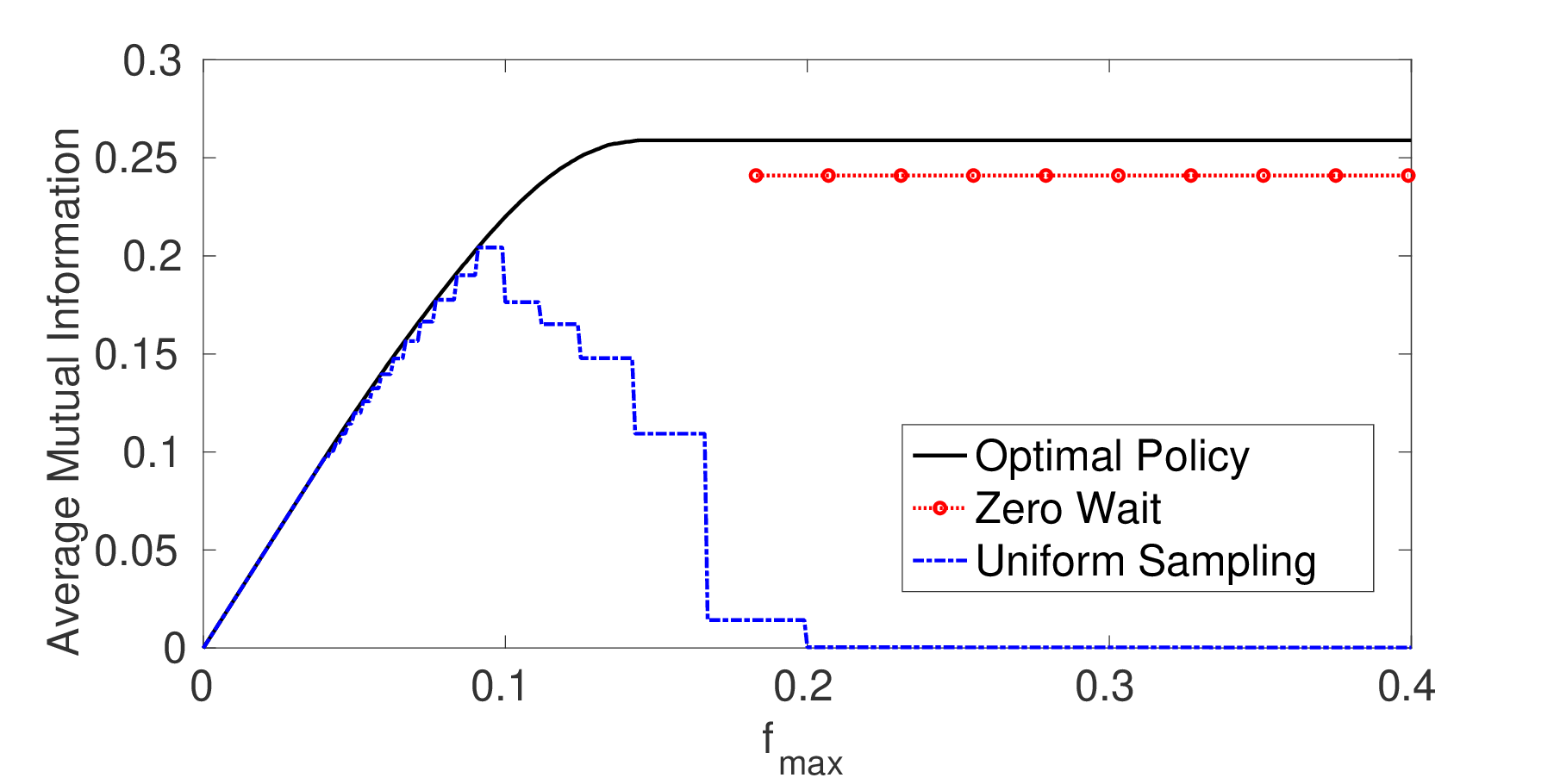 There are sampling policies that maximize the information and minimize the delay provided by every
sample in a sensing system. Depending on the distribution of network transmission times and the penalty
of delayed samples, zero-wait or uniform-wait policies are far from optimal. In fact, threshold
policies that account for the penalty and expected transmission time will often give much better
results.
There are sampling policies that maximize the information and minimize the delay provided by every
sample in a sensing system. Depending on the distribution of network transmission times and the penalty
of delayed samples, zero-wait or uniform-wait policies are far from optimal. In fact, threshold
policies that account for the penalty and expected transmission time will often give much better
results.
